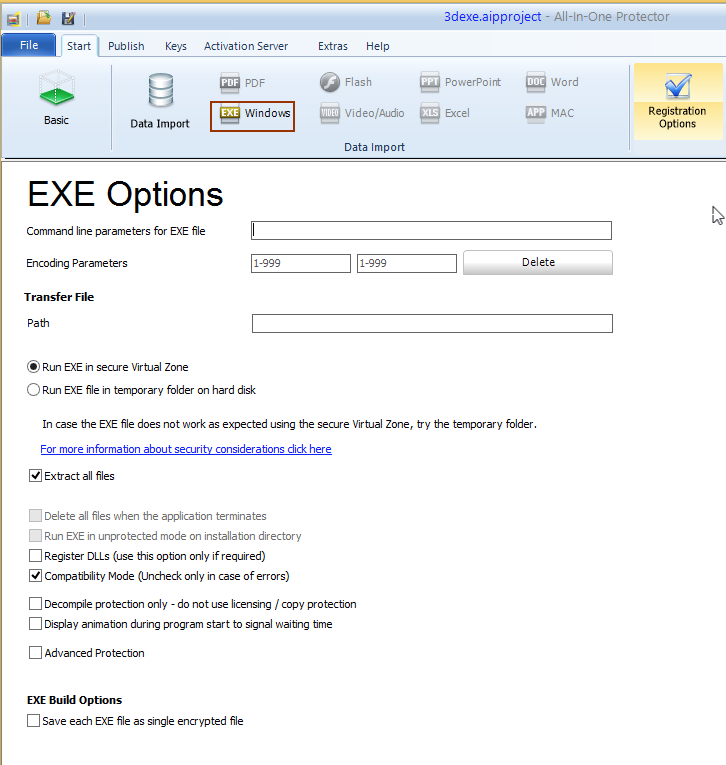
EXE files - protection options
There are different options you can use, depending how your application is structured.
Command Line Parameter for EXE file
A hard coded command line can be passed to the EXE file. If you use the variable %path%, the path where the EXE file starts is inserted.
The command line can also include encoding parameters (see below).
Transfer file and Encoding Parameter
This feature should be used if the EXE runs only with the option: Run EXE file in temporary folder on the hard disk or if you want to add an additional layer of security.
Encoding Parameters
Select random 3 digit numbers. The numbers should be different per project
Path
Path and file name of the text file. Instead of hard coding a path use one of the following variables
%1% = user documents folder - e.g. c:\users\admin\documents
%2% = appdata roaming folder - e.g. c:\users\admin\AppData\Roaming
The main application, which should be protected, can be invoked either by passing a command line parameter or an additional text file is provided. Both include encrypted values. The values change during each program start as they are calculated based on the system time. The main application has to validate the values and should only start, if the validation is correct.
Using the command line with the encrypted parameters is an alternative if reading a text file is not possible. If no path / file name is specified, the values are provided using the command line.
How it works
•The All-In-One Player application does the license and copy protection check •If everything is OK, It creates the text file (if configured) and launches the main application (start file) using a command line (if configured) •The values in the text file or command line are calculated every time when the application launches based on the system time and the defined encoding parameters •The main application reads the text file, deletes it and analyzes the values (formula see below) from the text file or from the command line •The main application only starts when the values are valid
Encrypted ValuesThe text file or the command line contains two encrypted values (time1 and time2). The values are separated with spaces.
Example: 1897 1996
The two values are calculated during the program start based on the values of two encoding parameters.and the system time. As each project has its own encoding parameters, the results can never be calculated without knowing the encoding parameters. Two values are required as the launch of the application can take time - e.g. the application is launched at 8:15 AM but it takes 30 seconds until the text file can be analyzed and the time is then 08:16. The value time1 is calculated based on the time when the text file is created and value time2 is one minute later.
You have to calculate the value for the validation using the following formula
Trunc((MMHH * Encoding Parameter1)/ Encoding Parameter2)
MM = Minute (must be double-digit) HH = Hour (must be double-digit)
Trunc = truncate position after decimal point
Compare the result with the value of time1 and time2 from the text file or command line . Either time1 or time2 must be identical with the calculated value.
Example The time is 8:16 AM
(1608 * 892) / 763 = 1879,86369...
Truncated value is 1879
Now compare the value your application calculated with both values provided by the text file or command line. One value has to match the value your application calculated.
If your application typically takes longer than one minute to launch, make a second calculation where you subtract one minute - e.g. time is 8:16 AM - calculate the values for 8:16 AM AND for 8:15 AM |
Runtime Options
•Details Run EXE on secure Virtual Zone
•Details Run EXE on temporary folder on hard disk
Additional Options
The options are available depending on the selected protection type (Virtual Zone / temporary folder).
Extract all files
All files are extracted to the Virtual Zone / temporary folder. After the file are extracted, the EXE file, which was marked as the start file, is started. If this option is not selected, only the start file is extracted.
Delete all files when EXE is terminated
After the file, which was marked as start file, is terminated, all files are deleted on the temporary folder. If the Virtual Zone is used, this is done automatically as the Virtual Zone is removed in the memory when the program terminates.
Run EXE unprotected on installation directory
This option extracts all files to the folder, from which the All-In-One Player was started. Then the file is unprotected.
One possibility for this option would be to protect an installer. The customer has to activate the software. Then the installer is extracted and starts. The files are unprotected after the installation.
Register DLLs
The Virtual Zone allows to register DLLs before the application starts. The registration is done in a virtual registry, which needs no administration rights. After the program terminates, the registry entries are removed.
This function does not work with all DLLs and should be used only, if DLLS have to be protected which have to be registered.
If the registration does not work, you have to remove the DLLs from the project and register + install it unprotected with an installer.
Compatibility Mode (Uncheck only in case of errors)
If the protected EXE file does not start, uncheck this option. In case the EXE file comes with a .config file, this option has to be checked.
Example: Myapp.exe and Myapp.exe.config
Decompile protection only - do not use licensing / copy protection
In case a single EXE file should only be protected against decompilation and no licensing should be used or the licensing is done by Licence Protector (www.Licence-Protector.com), then use this option. All licensing settings are ignored and no license file (.lic) is created.
Display animation during program start to signal waiting time
As the loading of a huge project can take a little bit longer, the display of an animation with text indicates the user, that the application will start soon.
Advanced Protection
This option checks, if the All-In-One Player file was modified (e.g. a hacker patched the file). In this case the protected application will not be started.
EXE Build Options
Save each EXE file as single encrypted file
Use this option only if you have multiple EXE files in the project but no additional files like DLLS, images etc. Each EXE file will use the same license file.